Just in time access for Office 365 privileged groups
Understanding who has access to your resources
Securing and managing membership of privileged groups and roles should be a priority for every organisation. Privileged groups and roles, those which provide elevated access to resources of which may be of sensitive or confidential nature, are vital for any IT department to function and provide administrators access to the services and data supporting the business.
Traditionally, IT departments utilise a security model whereby administrative permissions are permanently assigned irrespective of how often they are required, or accounts may have access enabled and revoked on an as needed basis, which is a manual process subject to human error. For both scenarios, because there are times where access is granted and not required, it provides a window of opportunity where these accounts could potentially be exploited and misused. Depending on the level of access assigned to these administrative accounts, and in some scenarios this access may be extremely powerful, this access may be used to not only access but also destroy or disseminate your organisations intellectual property, much of which is of a sensitive and confidential nature. There must be controls put in place to ensure these scenarios are unlikely to occur.
Providing automated mechanisms which are integrated into your identity management solution to securely control how access is granted to privileged groups is essential if you wish to proactively address when administrative account access is elevated, the length of time access is permitted prior to automatic revocation, and who has the authority to approve or deny such a request. Once implemented, the window of time where these accounts have elevated access is closely monitored, audited, and then restricted through a workflow process determined by an organisation based off their account management lifecycle requirements as part of their security policy.
Microsoft’s Identity Governance Offerings
Microsoft’s cloud-based identity management solution, Azure Active Directory, has several identity governance components which can be enabled with the appropriate licenses, either Enterprise Mobility + Security E5 or Azure Premium P2 (which is included in EMS E5). These license skews include features designed to protect and monitor accounts, including administrative accounts. There are four areas within Azure Active Directory Identity Governance including entitlement management, access reviews, terms of use, and privileged identity management.
In a recent article I discussed access reviews for guest access. You can read more here - For more information - Link to Access reviews for guest accounts
Privileged identity management provides the process to enable workflows to govern the lifecycle of how access is granted for privileged groups. Whilst it can be applied to Azure resources, this article concentrates on protecting administrator groups and roles within Azure Active Directory. Privileged identity management enables workflows whereby eligible accounts can request their access rights to be elevated for a specific administrative group or role. What happens once access has been enabled or approved is predicated by the configuration settings and rules assigned to each privileged group. This means there is scope to customise workflows based off the group or role affected. It may be prudent to have more stringent controls applied to groups with extremely high levels of access such as a global administrator and these controls can include how long access will be granted, whether it must be approved, a requirement to add justification for access, who should be notified when a change occurs, and the ability to allow an account to be eligible only during a specific date range
Privileged Identity Management considerations
Implementing new workflows impacting how people work requires careful consideration, including change management, to ensure successful adoption of the new processes and that they have minimal impact without causing business disruption. The education process should highlight that whilst enabling privileged identity managed increases overhead when granting and revoking access, it shouldn’t be seen as a negative as affected administrators should have a high focus towards enhancing security, and many tasks requiring elevated privileges should be well considered and pre-planned with approvals prior to execution.
Depending on how a workflow is configured, there can be multiple tasks performed by people required to complete the request and approval processes. Therefore, it’s essential that those involved, especially those who will be processing approval requests, understand their role and can complete tasks in a timely manner or prepare to have these tasks automated where possible, otherwise an inevitable breakdown in the process will occur which could lead to people questioning the additional layer of security.
Part of the process to enabling privileged identity management is to audit and review existing access across each administrative group and role to determine which accounts will be deemed eligible for access, those accounts requiring the new workflows for access to be granted, and those who will be assigned as permanent. Post review of the assigned access many accounts with existing permissions should be moved from permanent to eligible, thus ensuring accounts are only assigned elevated privileges when deemed necessary. On the contrary, there will be accounts allocated with permanent privileges where it makes sense to do so, and these accounts require quick and constant access to complete tasks.
Finally, enabling privileged identity management doesn’t need to be a blanket change across an organisation nor does it need to affect all groups and roles that provide elevated access. The change may be gradually rolled across each privileged group, it may be enabled for specific people or groups of people, or a combination of both. In additional to this, there should also be a requirement to have break glass accounts that bypass security controls in the event there is an issue with the security controls protecting Office 365.
Quick Facts
- Able to protect many administrative groups and role types, including global administrator
- Enterprise Mobility + Security (EMS) E5 or Azure Premium P2 license is required for each account utilising privileged identity management
- Azure Multi Factor Authentication is a requirement for those assigned the approval role
- Accounts may be assigned as eligible or permanent. Those who are assigned as eligible need to kick off a process to have access to the privileged group enabled, this may include approvals
- Elevated access may be assigned and revoked at predetermined date and time
- An accounts eligibility may be locked down to a specific date period
- Audit logs provide a history of when elevated access has been assigned and to whom
- Email notifications keep people informed of their outstanding tasks relating to privileged identity management
Privileged Identity Management Examples
Enabling assignment date ranges
Privileged identity management allows for flexibility when deciding how permissions assigned, either permanent or eligible, and for accounts assigned as eligible an additional control is put in place to define the date range this eligibility is valid.
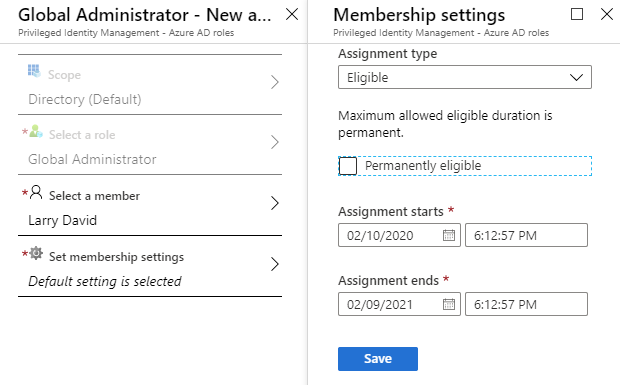
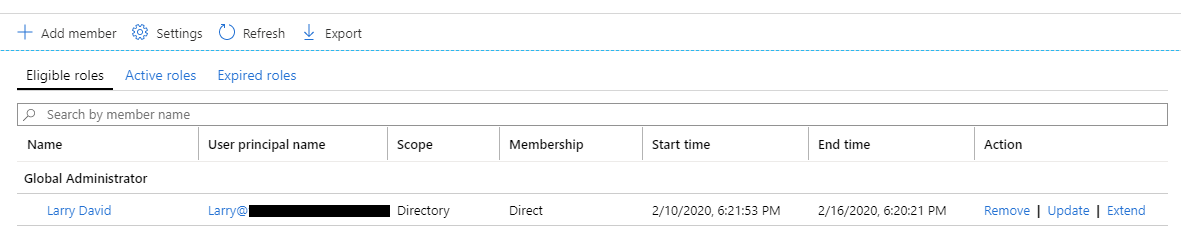
Role assignment Administration
Privileged identity management Administrators have control over administrative groups and roles to assign who has permanent access, who is eligible. Adding, removing, or modifying exiting assignments is performed via the Azure portal.
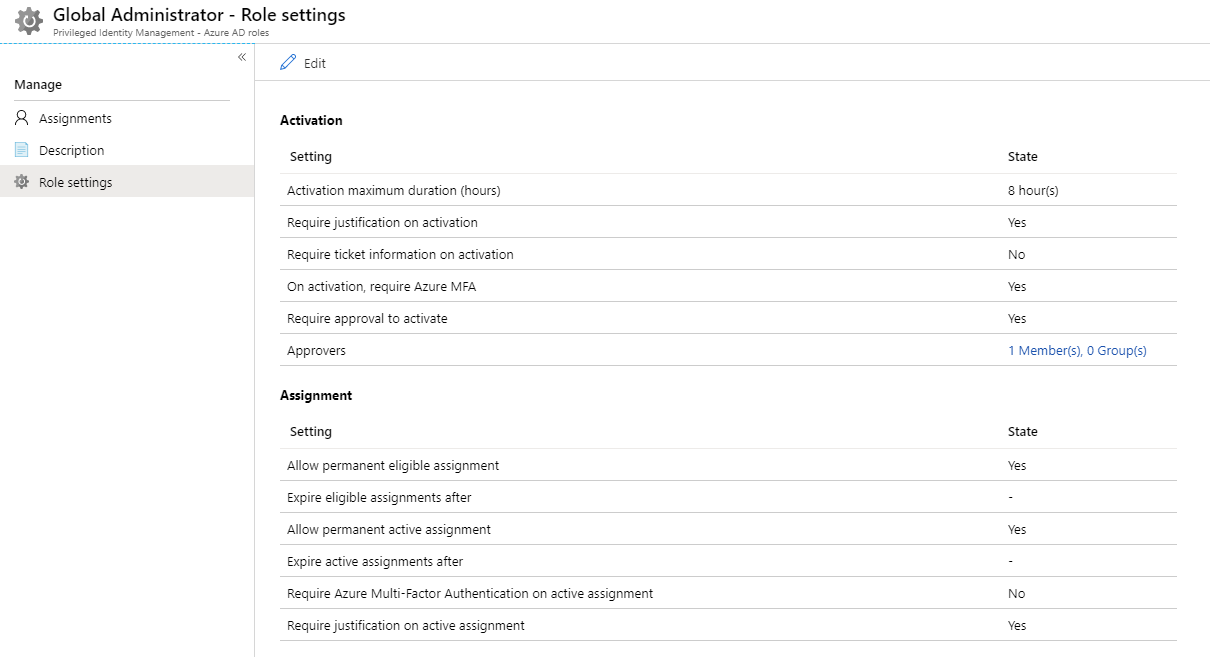
Group assignment configuration settings
Each administrative group and role contain multiple configuration options including how long an assignment is granted, whether approval is required, and who is able to approve requests.
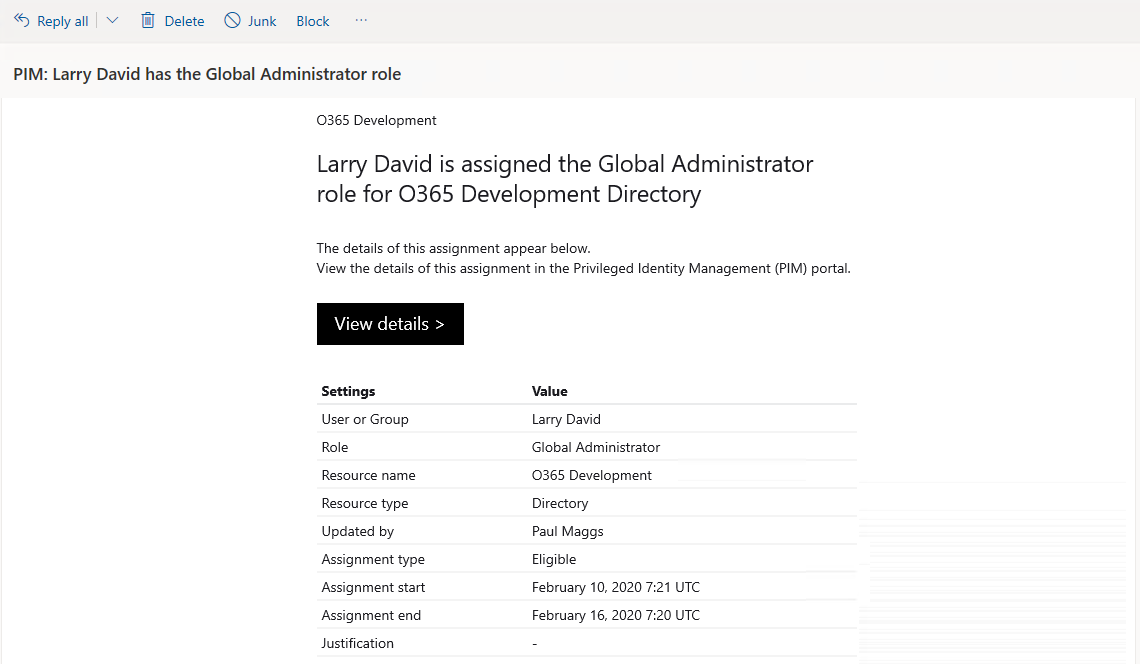
Notifications
Privileged identity management provides notifications of assignments and requested approved via email which redirect to the Azure portal. The Azure portal allows eligible accounts the ability to request access and approvers the ability to approve or reject requests.
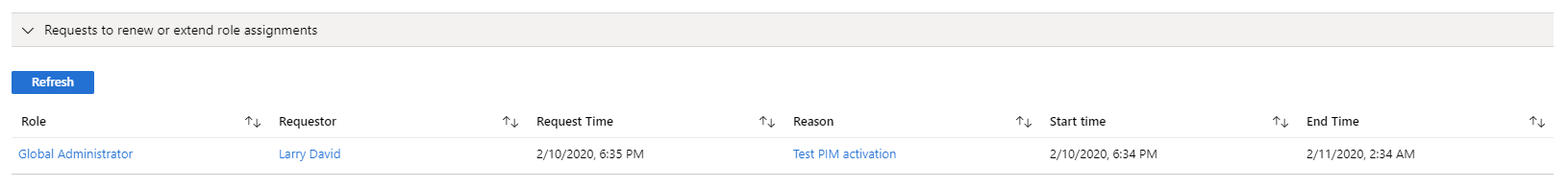
Approving requests
Approvers access the Azure portal to review and either approve or deny request from eligible accounts.
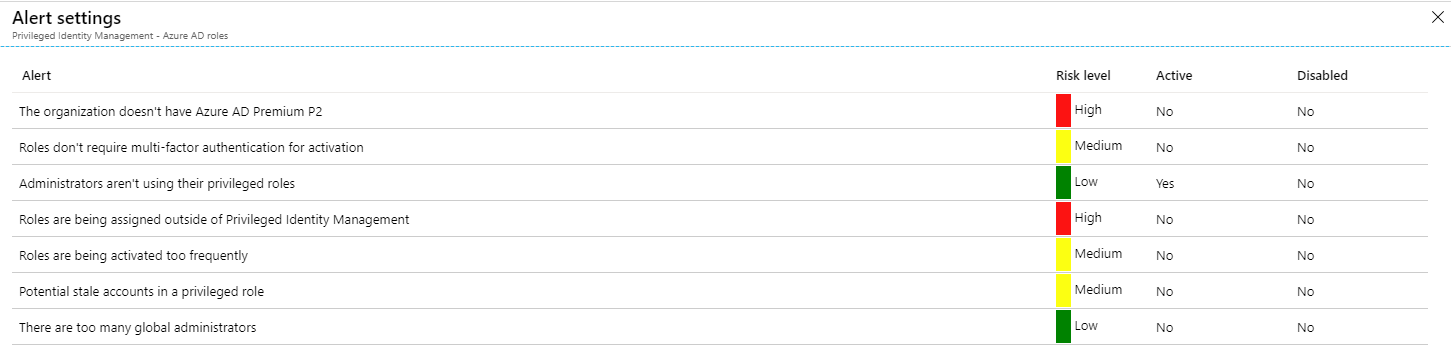
Alerts
Due to the sensitivity of the accounts associated with privileged identity management, built in alerts provide an overview of what’s occurring in the environment. Alerts includes topics such as administrative accounts not enabled for MDA, administrators who aren’t using their privileged roles, and roles activated too frequently.