Using Cloud Apps Security to restrict cut, copy, paste, printing, and file downloads from non-Intune compliant endpoints
Microsoft’s Cloud Apps Security (MCAS) extends the conditional access configuration and alerting capabilities provided by Azure Active Directory. Many organisations rely on conditional access to control the devices people use to access corporate data, and in many instances to block access if devices do not meet compliance requirements.
But what happens if blocking access from unmanaged devices is too restrictive? What if an organisation needs to continue to support access from these devices and can access be enabled in a secure manner? The answer is yes!
Multiple MCAS policy options support unmanaged devices accessing corporate data in a secure manner with mechanisms in place controlling the actions able to be performed, including whether content may be copied, printed, or whether files can be downloaded. Additional options available include securing a document when it is downloaded by automatically applying information protection, whereby encryption is applied to control who has access to documents regardless of where they are stored, to blocking access from desktop applications.
Other benefits when using MCAS conditional access policies include:
-
Quickly and easily define alerting rules, these may include MCAS alerts availalbe from the administration console, email alert, SMS alerting, and integration with Power Apps to orchestrate workflows
-
Alerts may be defined with a policy severity of either low, medium, or high. The policy severity assigned affects the overall individual investiagion score
-
Categorisation of alerts, for example DLP or Compliance to simplify reporting
-
Enable custom messaging when a policy is enforced to provide additional information to end users when an alert is triggered
Deploying MCAS conditional access policies is simple, yet there are several considerations required to ensure a successful implementation:
-
The Conditional Access App control apps, found in MCAS, must be populated with the cloud applications you will use for your future policies. Without enabling this feature you will not have the option to perform the block rules outlined in the examples later in this article.
-
Plan how you will scope your conditional access policies, both Active Directory conditional access and MCAS conditional access policies have scopring options determining how and where a policy is applied. You may find your Azure Active Directory conditional access policy routes all requests to MCAS which then defines the scope
Populating MCAS Conditional Access Apps Control apps
Before you can configure a MCAS conditional access policy, you will need to ensure the appropriate connected apps are available from your MCAS portal.
-
Sign into https://portal.cloudappsecurity.com
-
Expand Investigate, select Connected Apps, then select Conditional Access App Controls apps
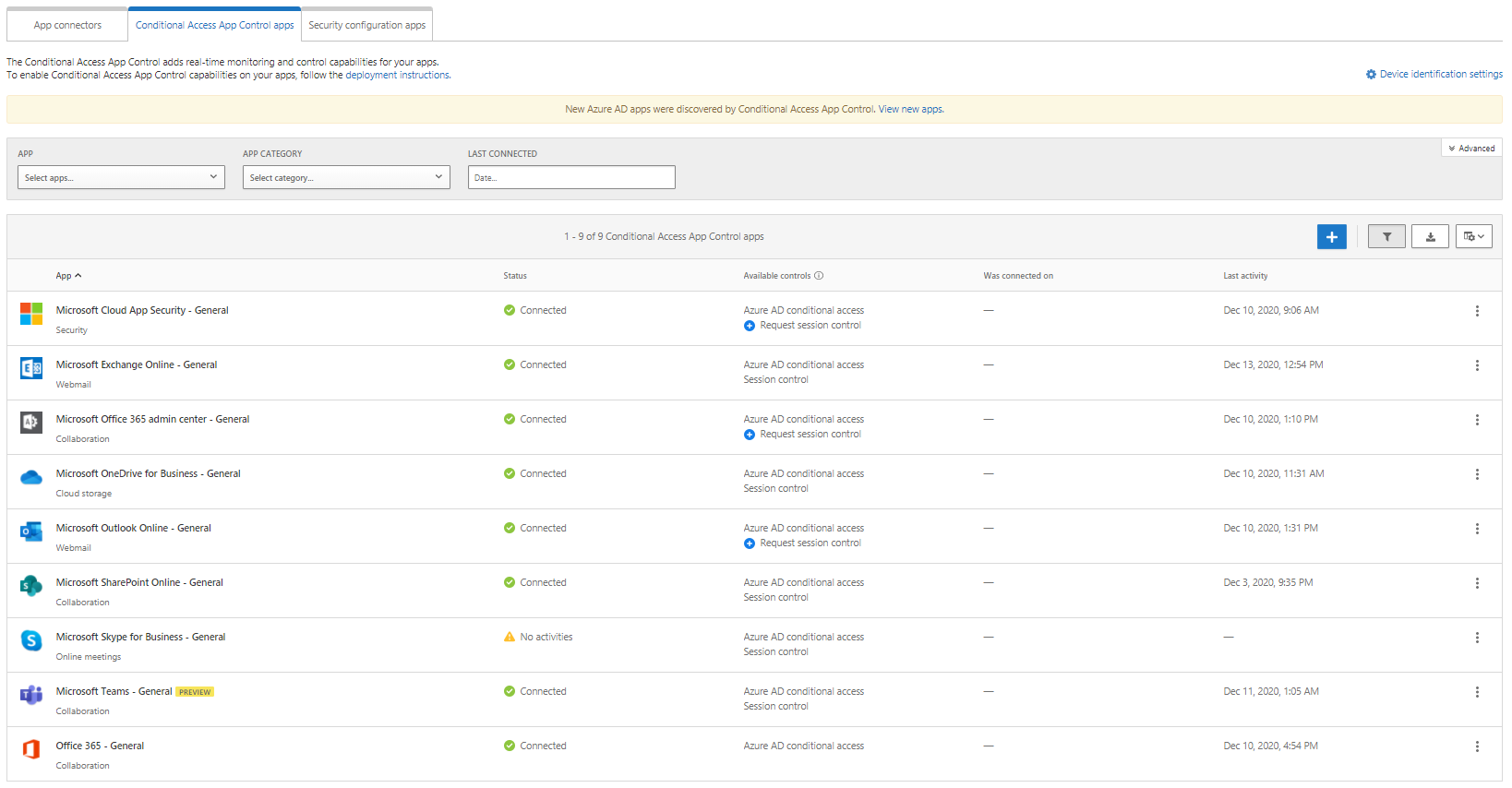 ×
×
If you do not see the application you want to control as part of your MCAS conditional access policy then you’ll need to create an Azure AD conditional access policy to route requests to MCAS prior to signing into the Office 365 service you want to include. Without this step you may not be able to configure the ‘Session control type’ required of the policy. This example highlights how to include Exchange Online:
-
Sign into https://portal.azure.com
-
Search for and open Azure AD Conditional Access
-
Create a new policy and use the following settings:
a. Users and groups: Scope to your test account, exempt any accounts a per your organisational policy, for example break glass
b. Cloud apps or actions: All cloud apps
c. Grant: Grant access (You will typically have other policies assigned enforcing MFA, etc)
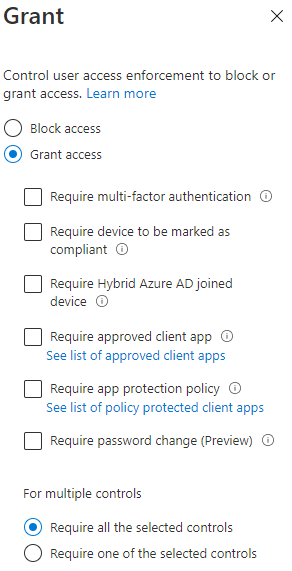 ×
×d. Session: Enable ‘Use Conditional Access App Control’, from the dropdown list choose ‘Use custom policy’
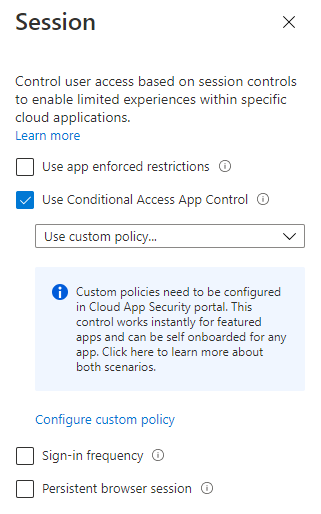 ×
× -
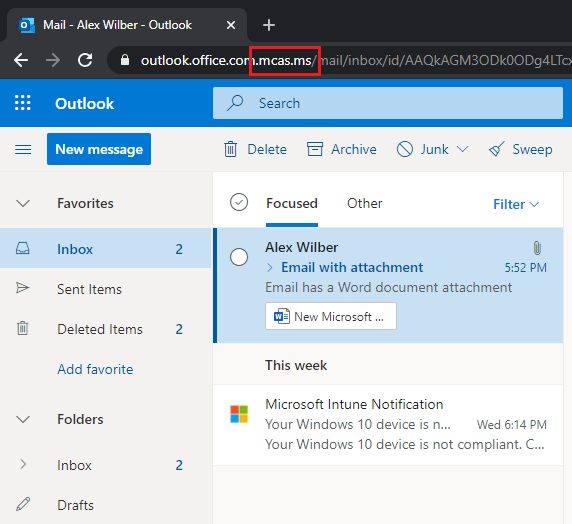
Sign into https://outlook.office.com to force Exchange Online to be included as a connected app. Ensure the Azure AD conditional access policy is correctly redirecting the session to MCAS by reviewing the URL, when working correctly the domain portion of the URL ends .mcas.ms
 ×
× -
Review your MCAS connected apps to ensure Exchange Online is now available as a conditional access app control app. You may repeat this step for other services you want to include in your policies
MCAS policy restricting cut, copy, paste, and print
Prior to completing this step, ensure the application you want to control is displayed as a conditional access app control app, located under connected apps. See the steps Populating MCAS Conditional Access Apps Control apps if you need to enable this functionality by creating an Azure AD conditional access policy to route requests to MCAS.
Be aware these policies disable cut, copy, and paste between multiple Office 365 browser sessions, for example you cannot open Outlook and Teams as separate browser tabs and then copy content from Outlook into Teams, and vice versa.
This example will block cut, copy, paste, and printing for the test account specified in the Azure AD conditional access policy when accessed from a non-Intune compliant device.
Complete the following steps to create policy blocking cut, copy, paste, and printing:
-
Sign into https://portal.cloudappsecurity.com
-
Expand Policies
-
Select Create policy, select Session policy
-
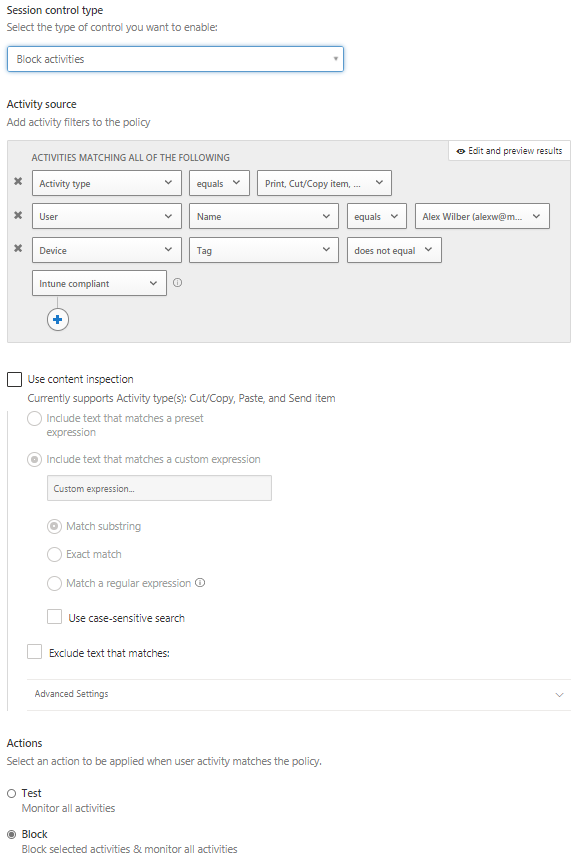
From the Policy template drop down, select Block cut/copy and paste based on real-time content inspection. Accept the policy template when prompted, provide a policy name
-
Configure the Policy severity as low and Category as DLP
-
The session control type should automatically be configured as Block activities
-
Configure the Activity source with the following settings
a. Activity type equals Cut/Copy item, Paste item, Print
b. User Name equals ‘Add your test user account’
c. Device Tag does not equal Intune compliant
-
Uncheck ‘Use content inspection’.
-
Configure Actions as Block, you may also select a custom message to be displayed when a violation is detected.
-
Enable alerts, however, for this example email and SMS alerts will not be enabled
Example Policy:
MCAS policy restricting file downloads
This example blocks file downloads when attempted by the test account specified in the Azure AD conditional access policy from a non-Intune compliant device.
This policy targets all file downloads, however, it is possible to scope restrictions for specific document types which is out of scope of this article.
Complete the following steps to create a policy blocking all file downloads:
-
Sign into https://portal.cloudappsecurity.com
-
Expand Policies
-
Select Create policy, then select Session policy
-
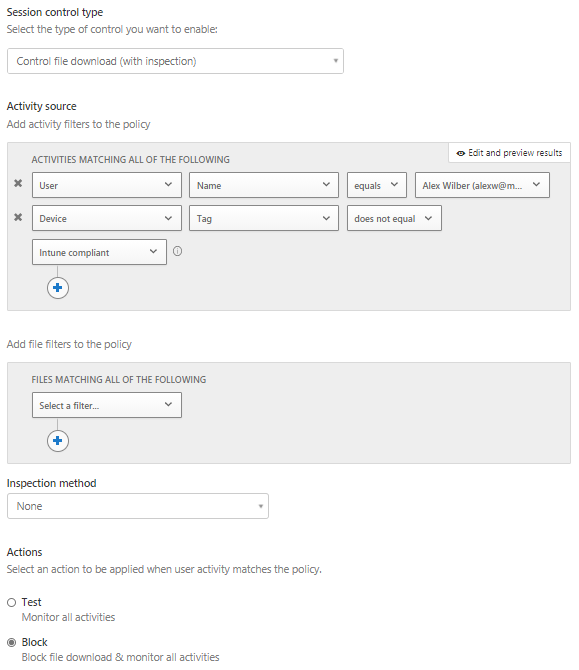
From the Policy template drop down, select Block cut/copy and paste based on real-time content inspection. Accept the policy template when prompted, provide a policy name
-
Configure the Policy severity as low and Category as DLP
-
The session control type should automatically be configured as Control file download (with inspection)
-
Configure the Activity source with the following settings:
a. User Name equals ‘Add your test user account’
b. Device Tag does not equal Intune compliant
-
Do not add any file filters
-
Inspection method is configured as None
-
Configure Actions as ‘Block’, you may also select a custom message to be displayed when a violation is detected. Notice the file options has an option to protect, this allows classification labels to be applied to downloads.
-
Enable alerts, however, for this example email and SMS alerts will not be enabled
Example Policy:
MCAS Policy Examples
Once the policies are deployed you can perform functional tests to validate the configuration is correct. To do so, complete the following tasks:
-
Sign into https://outlook.office.com
-
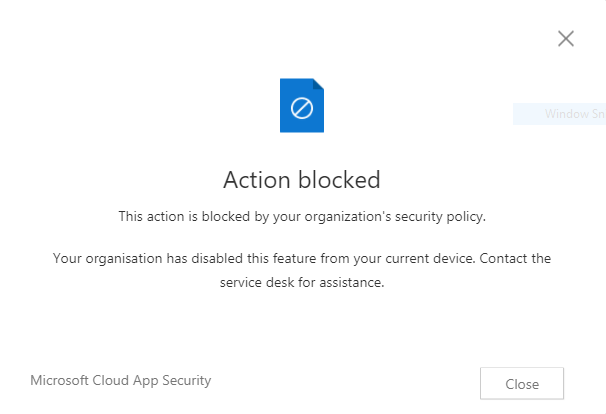
Open an email and attempt to copy the contents to the clipboard. A block message will appear as per below
 ×
× -
Whilst viewing the email, select more options (…) dropdown, then select Print. Once the email is displayed in print view, select Print
-
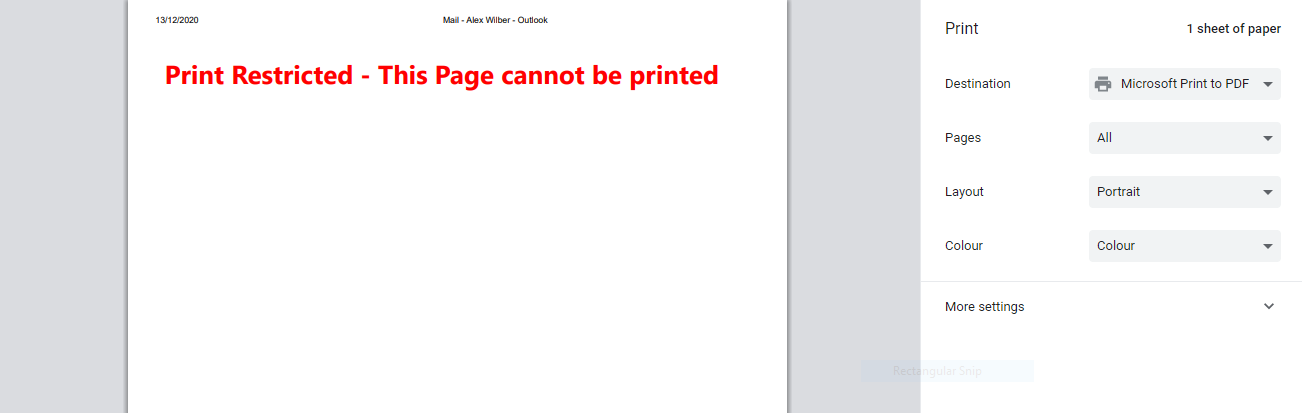
The print preview displays the message stating the action is blocked as per below
 ×
× -
Select New message, add a Word document as an attachment. Send the document to yourself.
-
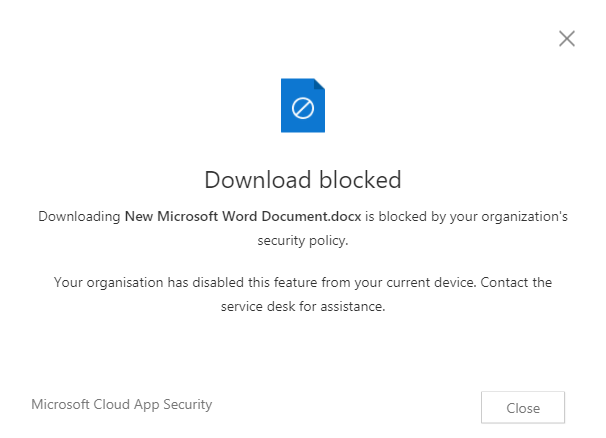
Open the email containing the attachment, attempt to download the file. A block message will appear as per below
 ×
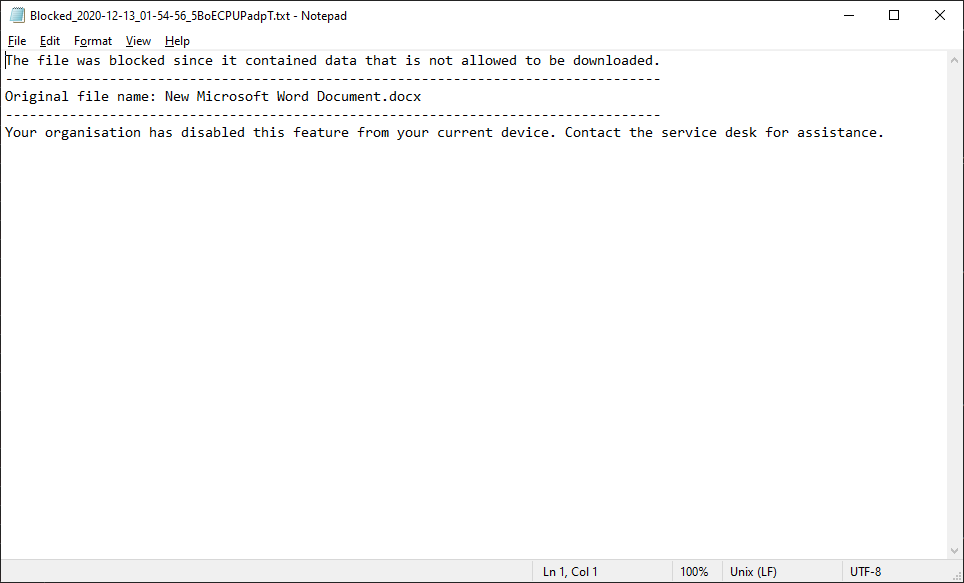
×In additional to the block message, a text file is downloaded providing further details:
 ×
×
MCAS Alerts
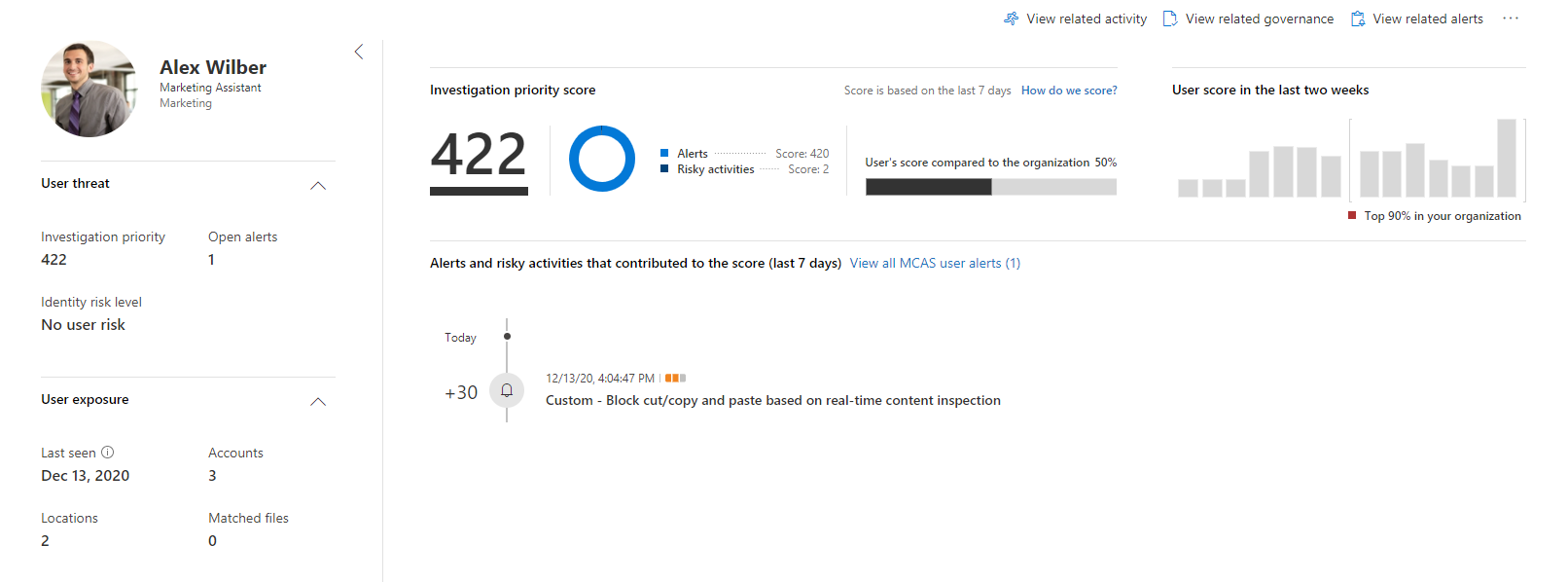
If you enabled alerting for your MCAS policies, the output will resemble the examples shown below. Notice there is a difference in the alert time showing in the dashboard (when the alert arrives into the dashboard) and the alert time when review the alert details (when the alert was triggered by the policy), so keep this in mind when performing investigations:
The alert from the dashboard:
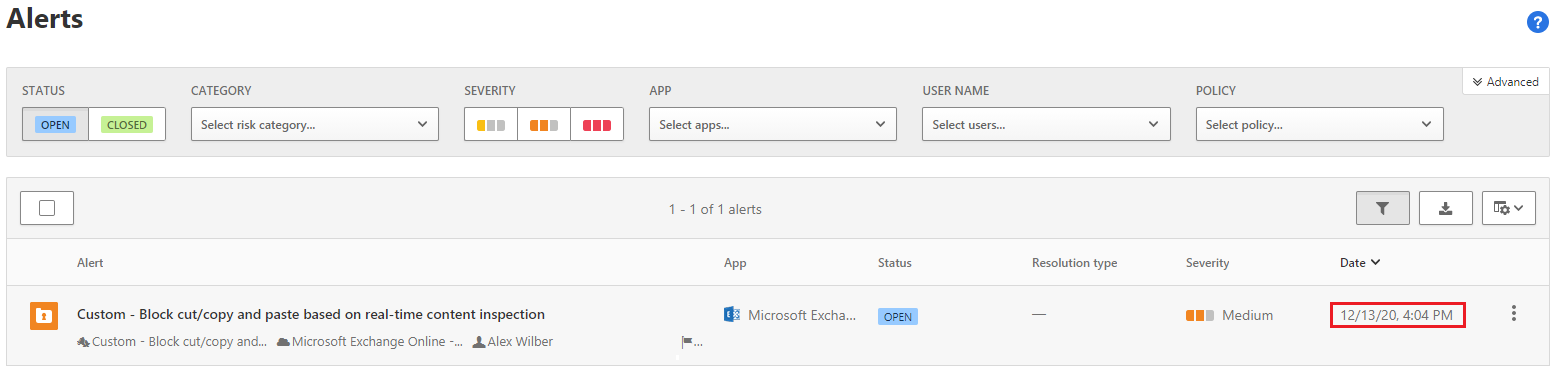
Selecting the alert provides additional information:
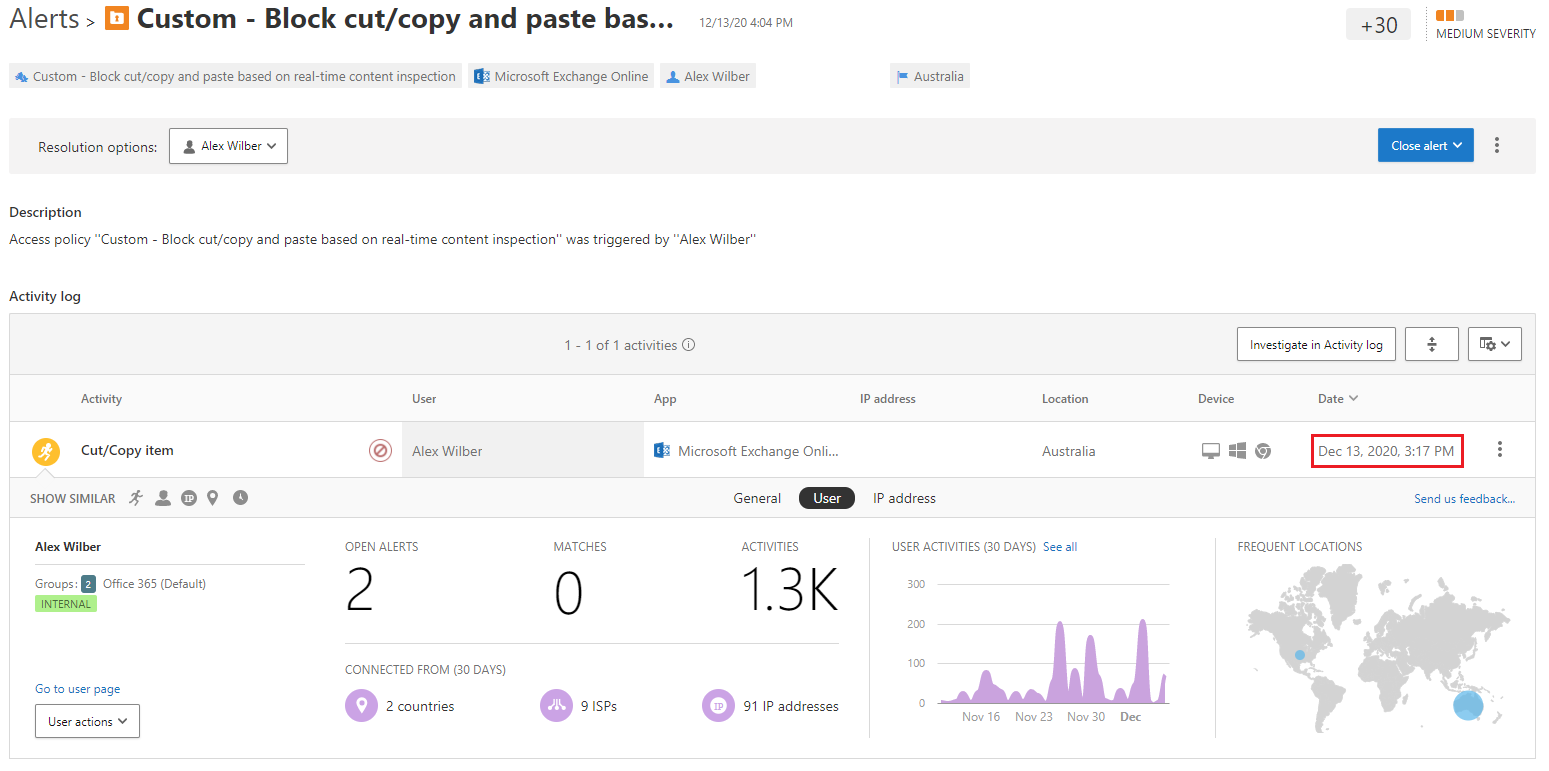
An accounts investigation score is derived from all alert scores accumulated within the previous 7 days. The following example shows the block cut/copy and paste alert contributed 30 points to the total score of 422. Combined with other policies the investigation score highlights accounts performing activities which may be deemed risky and require further investigaton.