Restricting desktop applications with Cloud App Security conditional access
Many organisations restrict access to Office 365 services and applications from unmanaged or non-compliant endpoints through the use of Azure AD conditional access policies. In additional to these traditional conditional access policies, Cloud Apps Security (CAS) extends these capabilities with additional features, including custom block messages and custom alerts surfaced from within the CAS administration portal.
CAS policies are broken down into session policies (those which affect web browser sessions) or access policies (those which affect desktop applications) and are applied to access attempts against Office 365 applications and services such as Microsoft OneDrive for Business, Microsoft Exchange Online, Microsoft SharePoint Online, and Microsoft Teams. The typical function of these policies is to either monitor or block access or access attempts.
Whilst CAS conditional access policies provide similar functionality as traditional Azure AD conditional access policies, there are some feature differences which may make them more appealing, including:
-
The dialogue displayed when an attempt to access a restricted resource is more user friendly than the traditional messaging
-
The message displayed when access is blocked may be customised, unfortunately the number of characters you can use in a message is limited, however, it does allow you to put in a brief descriptive message
-
Several alerting options exist, including the ability to extend further with email notifications or Power Automate, which are surfaced from the Cloud App Security portal. These alerts are simple to enable and surface useful details about the session or access request.
In this article I will provide an overview of how to enable a Cloud Apps Security access policy restricting access from Office desktop applications accessing Office 365.
Before you do deploy a CAS conditional access policy, several tasks must be completed to ensure you’ll be presented with the correct configuration options during policy:
-
An Azure AD conditional access policy is required to capture the access request during authentication and redirect the session to Cloud App Security.
-
You cannot configure an Office 365 application or service as part of a CAS conditional access policy, such as Exchange Online, unless it is registered as a CAS connected app. Therefore, before deploying any policy, and only after you have deployed the Azure AD conditional access policy outlined above, sign into the Office 365 application or service you want to register as a connected app.
Deploying a CAS Conditional Access Policy
The following example outlines how to deploy a CAS conditional access policy. This scenario blocks access from an unmanaged Windows 10 endpoint when attempting to access an Office 365 service via a desktop application, such as Outlook. When access is blocked
When Cloud Apps Security receives a sign in meeting the criteria to block access, for this example when attempting to use an Office 365 desktop application to access Exchange Online, the notification is more informative as Cloud Apps Security allows customisation of the messaging displayed.
For this example the message is customised to include “You are attempting to access Office 365 from a desktop PC that does not meet your organisation’s compliance requirements.”
An example cloud apps security notification:
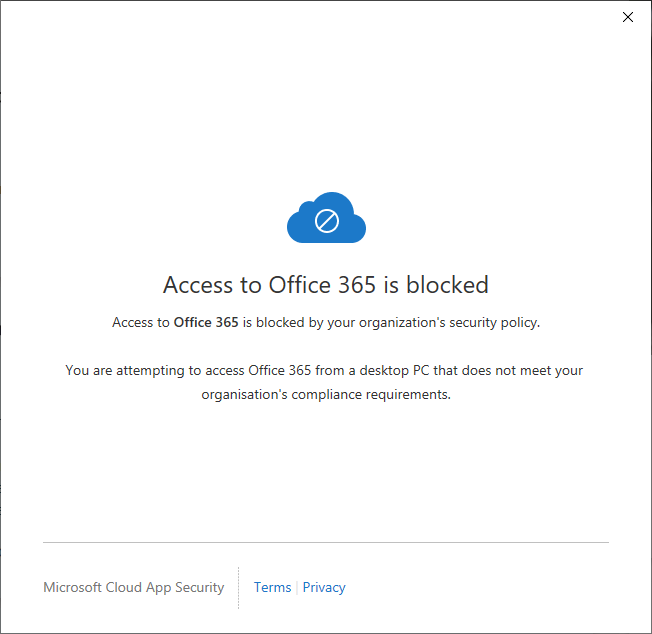
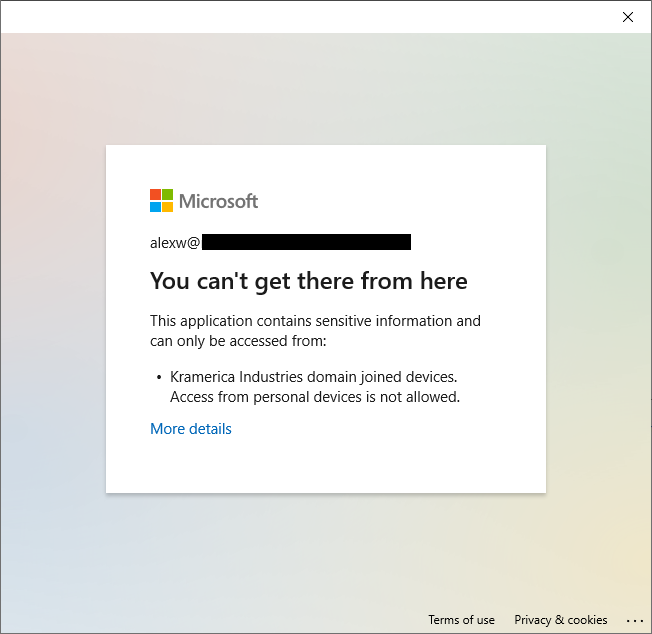
The notification displayed by an Azure AD conditional access policy is not as user friendly as a Cloud Apps Security access policy, however selecting more details does provide additional troubleshooting information which may be beneficial for the service desk:
Configuring Azure AD Conditional Access
Prior to enalbing the Cloud Apps Security access policy, an Azure AD ‘conditional access’ policy must be deployed to re-route requests to Cloud Apps Security.
Create a new Azure AD conditional access policy with the following configuration:
-
User and groups configured to include who should be affected by this policy. As a best practice include break glass account(s) into the exclude list
-
Cloud apps or actions includes ‘All cloud Apps’
-
Conditions has no configuration settings enabled
-
Grant has no configuration settings enabled
-
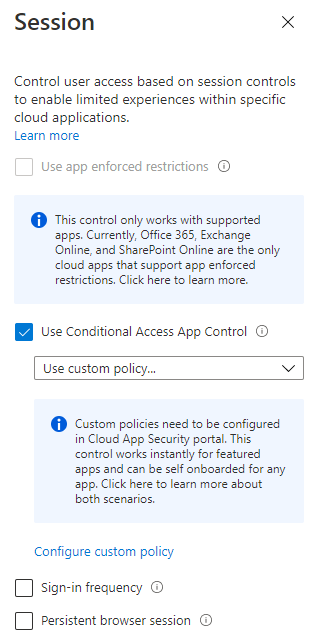
Session must have ‘Use Conditional Access App Control’ enabled and configured as ‘Use custom policy’
When custom policy is enabled, the following message is displayed:
‘Custom policies need to be configured in Cloud App Security portal. This control works instantly for featured apps and can be self onboarded for any app. Click here to learn more about both scenarios.'
Configuring Cloud Apps Security Access Policy
Conditional Access App Control Apps
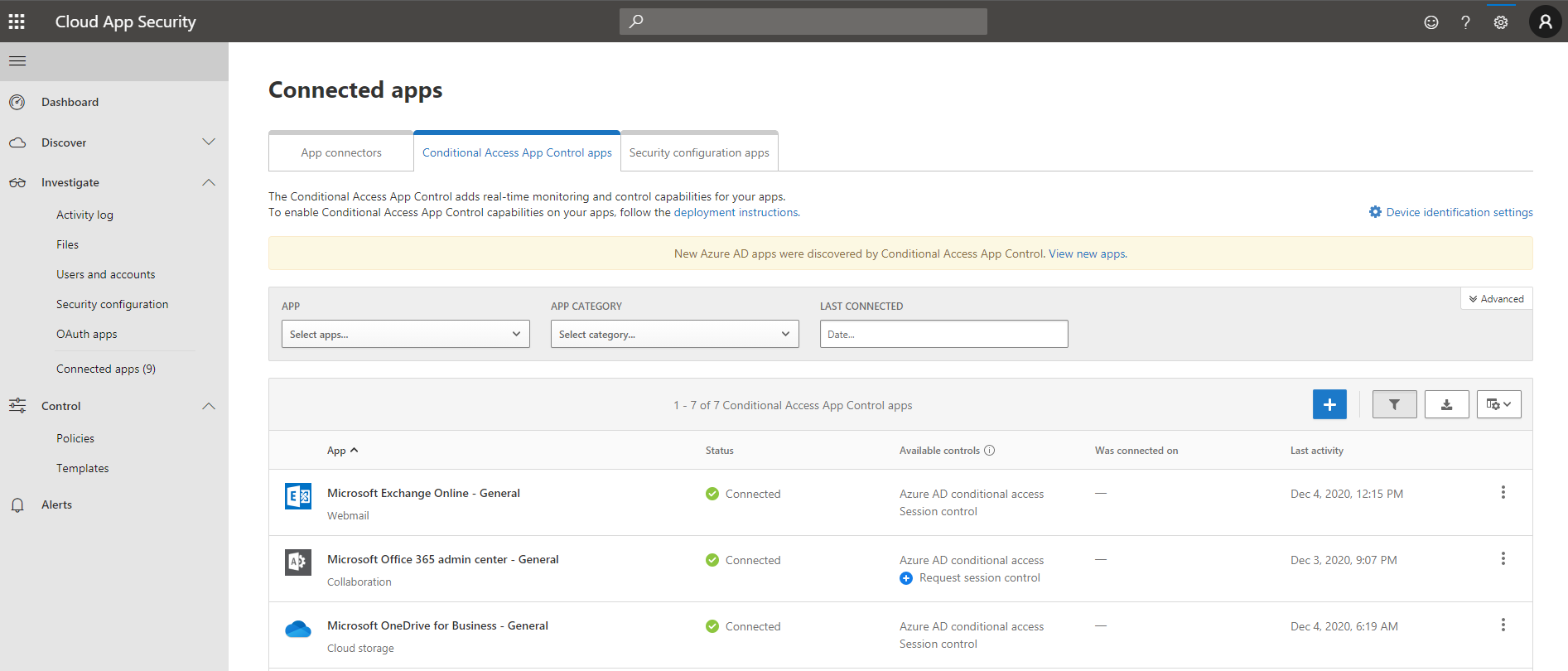
Prior to the creation of the access policy, ensure the application whose access you wish to control is displayed under ‘Conditional Access App Control apps’ from ‘Connected Apps’. To do this, perform the following steps:
-
Sign into https://portal.cloudappsecurity.com
-
Expand Investigate, select Connected apps, and then Conditional Access App Control apps.
A list of connected apps is displayed. E.g. Office 365 General, Microsoft SharePoint Online - General, or Microsoft Teams - General.
If no applications are displayed or an application you wish to control via a Cloud Apps Security policy, then proceed with the next step. If the application you wish to control is displayed then you may continue to deploy the access policy.
-
Ensure the Azure AD conditional access policy is enabled and targeting the account you will used to perform the next steps.
a. Open a web browser and sign into https://outlook.office.com
b. Repeat the above step for other applicatiosn you wish to control, for example, https://teams.microsoft.com
c. Repeat steps 1 though 2 and ensure the Microsoft applications you signed into during steps 3(a) through 3 (b) are showing under Conditional Access App Control apps. Once showing they may be configured as part of the access controls.
 ×
×
Cloud App Security Conditional Access
-
From the Cloud Apps Security portal, expand Control, and then Policies
-
Click on the Create policy drop down, then select Access policy
-
Configure the following settings:
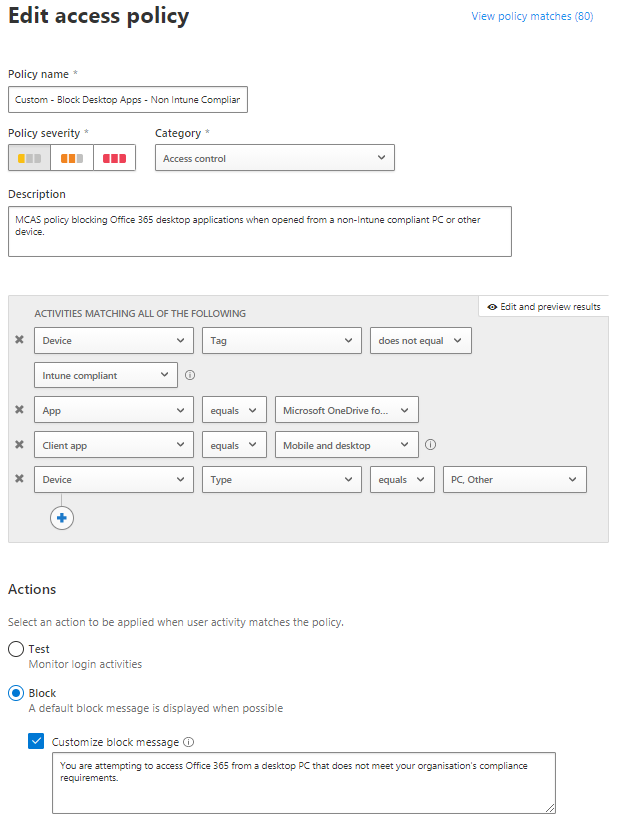
a. Policy name: Custom - Block Desktop Apps - Non Intune Compliant
b. Policy severity: Low severity
c. Category: Access control
d. Description: MCAS policy blocking Offie 365 desktop applications when opened from a non-Intune compliant PC or other device.
e. Activities matching all of the following
'Device tag' does not equal 'Intune compliant' 'App' equals 'Microsoft Online Services' 'Client app' equals 'Mobile and desktop' 'Device Type' equals 'PC, Other' *note: If required the rule can be further scoped to specific users or groups.*f. Actions: Block, and select Customize block message
"You are attempting to access Office 365 from a desktop PC that does not meet your organisation's compliance requirements."g. Enable ‘Create an alert for each matching event with the policy severity’. This will enable you to review alerts generated by this policy.
 ×
×